- Hughesnet Community
- :
- Hughesnet Support Community
- :
- General Discussion
- :
- Re: Zombie spam
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Zombie spam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Zombie spam
If you've heard me use the term 'zombie spam'. Well, here's a great example of it (just checked my spam log):
[Thu Sep 28 18:47:47 2017 GMT] "Tasha" <Tashadsm@bestel.com.mx> [189.204.161.48, bestel.com.mx, xxxxxxxPYxx], Subject: hey [Thu Sep 28 19:01:14 2017 GMT] "Tasha" <Tashaywhz@redcotel.bo> [190.103.68.103, redcotel.bo, xxxxxxxPNxx], Subject: hey [Thu Sep 28 19:10:40 2017 GMT] "Tasha" <Tasharg@vnpt-hanoi.com.vn> [113.190.240.220, vdc.com.vn, xxxxxxxxNxx], Subject: hey [Thu Sep 28 19:28:56 2017 GMT] "Tasha" <Tashayw@dmrcom.com> [199.21.155.170, dmrcom.com, xxxxxxxxNxx], Subject: hey
In the square brackets are the IP of the email server that sent it to me (can't be forged), the parent domain, and some SpamAssassin flags that I look for. In this case N = RDNS_NONE, Y = RDNS_DYNAMIC, P = HELO_DYNAMIC_SPLIT_IP (I look for about ten different signatures to determine if it's spam).
For me, they usually hit in groups of four, in a short period of time, from geographically disparate places.
Usually has a forged email address with a common name (Tasha, here) and the domain of the parent email server in order to fake SPF and RDNS detection.
This happens when someone sends a signal to those with infected computers, which in turn send these out completely without the host user even knowing it.
Lately these have been used as a precursor to massive bursts of activity for a couple of days, promoting some ridiculous stock that nobody's ever heard of. I saw two of these test bursts yesterday.
Hold onto your hats, it should be a fun weekend.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tasha likes you! 😛
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Stock Zombie is back, using open relays from Vietnam, Indonesia, India and Brazil:
[Thu Oct 19 07:11:33 2017 GMT] "Gregory Fischer" <Fischervsei@static.vnpt.vn> [14.171.160.232, vnpt.vn, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow? [Thu Oct 19 07:20:39 2017 GMT] "Peggy Hurst" <Hurstiolve@cc-kft.com> [103.19.109.112, netciti.co.id, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow? [Thu Oct 19 07:27:07 2017 GMT] "Constance Berg" <Bergak@ezfreecoupons.com> [103.233.116.142, upinfomax.in, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow? [Thu Oct 19 08:29:05 2017 GMT] "Ila Sloan" <Sloanklwhs@static.vnpt.vn> [222.254.238.121, vnpt.vn, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow? [Thu Oct 19 09:48:13 2017 GMT] "Anderson Calderon" <Calderonvumz@static.vnpt.vn> [14.237.11.80, vnpt.vn, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow? [Thu Oct 19 10:14:07 2017 GMT] "Nelson Mcmillan" <Mcmillanmxdsj@ondernemersgala.nl> [189.60.86.139, virtua.com.br, xxxxxxxxNxx], Subject: Seriously... What if this company went tenfold by tomorrow?
Hate these guys.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
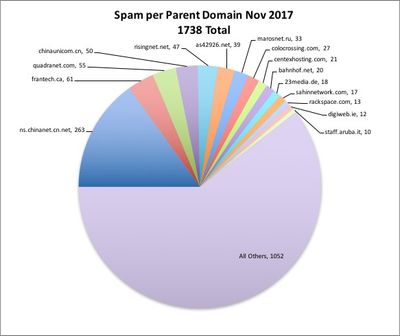
Overall spam count for Nov: 1738, mostly from China, which is basically one massive spamhaus.
Edit: I should point out that this is what my trap caught. Only 9 actually made it through to my junk box, which also happens to illustrate why I wrote the trap to begin with.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MarkJFine wrote:
Edit: I should point out that this is what my trap caught. Only 9 actually made it through to my junk box, which also happens to illustrate why I wrote the trap to begin with.
Only nine. SMH. That would be SOOOO nice. Seventy one so far today for me. LOL. And I've given up blocking them, as MSN can only block so many addresses and/or domains.
My only option? Chaging my main email from my MSN adress to Gmail, as I get ZERO junk mail at my Gmail address, at least at this point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've had my main email, run on a semi-private server since before 2000, and have used it for every bloody subscription signup and login imaginable since. Not to mention that the web site it used to be associated with used to get hit by scrapers and I'd never protected my DNS record (to so now would be ridiculously ineffective), although my email is linked to a specific domain using an SPF record. Some stupid email systems don't check the SPF record to see if a faked email using my address follows the SPF record and sends me a bounce message anyway - I count those as part of the total.
I set up the system in the email to do several things:
1. Only allow whitelisted email addresses thru to the inbox, everything else should initially be considered spam.
2. If it's using my email address and isn't from my email server's IP, it's automatically spam and goes to /dev/nul.
3. They run SpamAssassin on every email, which leaves the tags of each test in the email header.
I don't use SA's ranking system. If it contains any of the following, it's automatically spam and should be sent to /dev/nul - especially RDNS_NONE, which basically means from an open relay (99% of them):
URIBL_ABUSE_SURBL, URIBL_DBL_SPAM, URIBL_INV, URIBL_SBL, URIBL_SBL_A, URIBL_DBL_ABUSE_SPAM, URIBL_DBL_ABUSE_REDIR, RCVD_HELO_IP_MISMATCH, HELO_DYNAMIC_IPADDR, HELO_DYNAMIC_IPADDR2, HELO_DYNAMIC_SPLIT_IP, RDNS_NONE, RDNS_DYNAMIC, URI_ONLY_MSGID_MALF, BOUNCE_MESSAGE
4. Barring those, I also check the IP address my server received it from, which is really hard to spoof, and I check it against a mini DNS lookup of sorts that I've been building since April. It converts the IP to a parent domain (that you see in the graphic). If the parent domain is on a special block list send it directly to /dev/nul.
5. Last test, if everything else passes, I check a list of email address partials (some include before the '@', some include the faked domain). If any part of the 'From:' matches anything on the list - /dev/nul.
All of these get logged using the format you've seen earlier so I can collect statistics on how the system is doing and can routinely update the mini-DNS if the IP results in a domain it doesn't know about yet. That mini-DNS has grown to a 99k text file, containing a regex lookup of IP ranges, abuse email, domain, and a comment. Was originally going to have the system automatically route the email to the abuse email address, but I found that just makes things worse in many instances.
Everything else goes to junk just in case someone's used a new email address not on the whitelist, which happens a lot, but some still sneak thru. Those are usually the "dear beneficiary" or some of the zombies made to look like they came from your printer/voice mail, or the zombies where the 'From' includes the name of someone you know - how they do that is a complete mystery to me. That last one usually contains a link luring you to an infected site, which SA should detect and trigger one of the URI flags, but half the time it doesn't and they scoot through.
Nonetheless, as you said, only 9 out of over 1700 in a month... I'd say it's pretty effective.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where do these spams come from? They come from lists, compiled from scammers that compile lists like this:
--------8<----------
Hi,
DivTECH LLC is the world's most comprehensive directory of business information on people and companies. As part of our commitment to your privacy and your ability to control online information about yourself, we wanted to let you know (or remind you) that your business profile has been included.
Profiles are created in an automated process using publicly available information on web sources and contributions from the community. As a member of our directory, we would like to share valuable and relevant industry news with you from time to time. In addition, we often have the opportunity to supply information about interesting products and services from business partners, and we will occasionally share your email address with them if we think the information will be relevant to you.
As always, DivTECH respects your privacy and email communication preferences. All DivTECH email communications contain easy opt-out links so you may quickly and securely unsubscribe from receiving these emails at any time. If you would like to opt out your email address from our business directory.
Thank you for your time,
DivTECH LLC
DivTECH LLC, PO Box 182, Weymouth, MA, 02190, United States
If you do not want to receive emails from DivTECH LLC you may unsubscribe at any time.
--------8<----------
The company is listed as a valid marketing company, and has a presence on LinkedIn and Facebook. It likely scans and collects email addresses from both sites.
From all appearences this looks like a valid 'opt out' email, until you see that the From: <noreply@divtech-email.net>, and the Return-Path: <bounce@elgprovider18.com> don't match.
The email traces back to a domain of smtp124.emailtrack97.com which passes the SPF authorization test, but is under a domain parent of 'Clickback Inc.', a known spam generator.
Bottom line: Clicking that link to 'unsubscribe' (I've removed it here) does nothing more than to verify your email address for even more spam. Ignoring it is the safest thing to do since it neither confirms nor denies your existence.
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Where do these spams come from? They come from lists, compiled from scammers that compile lists like this"
And here I was hoping they came from actual zombies.... 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Lol... Technically what I just descried was where all spam comes from in general.
Zombies are usually generated from viruses and malware: Basically clicking on links in emails, images downloaded in emails (<- never, ever have your mail client automatically download images in an email), and sketchy web sites.
Zombies tend to come from people's infected computers, phones, and tablets rather than server sites (spamhauses).
* Disclaimer: I am a HughesNet customer and not a HughesNet employee. All of my comments are my own and do not necessarily represent HughesNet in any way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No no no no no...you're not understanding zombies at all. Zombies are reanimated human corpses. Clearly they can send spam. 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I love Monty Pyhton. Growing up with grandparents and a mother who is British, I tended to see it a lot.
What is the airspeed velocity of an unladen swallow? 😛
- Hughesnet Community
- :
- Hughesnet Support Community
- :
- General Discussion
- :
- Re: Zombie spam